Social Engineering: The Art of Human Hacking
Manipulate people into doing something, rather than by breaking in using technical means .Social engineering is the art of gaining access to buildings,
systems or data by exploiting human psychology, rather than by breaking in or using technical hacking techniques. For example, instead of trying to find
software vulnerability, a social engineer might call an employee and pose as an IT support person, trying to trick the employee into divulging his
password. The goal is always to gain the trust of one or more of your employees.
Kevin Mitnick
said
, "The weakest link in the security chain is the human element".
In a system, there is hardware, software and wetware, wetware being the human element of the system. With million dollar security systems and state of the
art security technology, the first two systems may be impenetrable, but with enough patience and knowledge, asocial engineer can use weaknesses in the
wetware to trick an unsuspecting target into revealing sensitive information. Social engineering is a use of psychological knowledge to trick a target into
trusting the engineer, and ultimately revealing information.
Social Engineering includes scams such as obtaining a password by pretending to be an employee, leveraging social media to identify new employees more
easily tricked into providing customer information, and any other attempt to breach security by gaining trust.
“You could spend a fortune purchasing technology and services...and your network infrastructure could still remain vulnerable to old-fashioned
manipulation.”
Social Engineering is the art of exploiting the weakest link of information security systems: the people who are using them. Social Engineering is a method
of gathering information and performing attacks against Information and Information Systems. An immense amount of loss has suffered by Organizations and
Individuals from these attacks. However Social Engineering as a threat is overlooked because of low awareness and lack of proper training for people.
What Social Engineers Want?
The goal for many social engineers is to obtain personal information that can either directly lead them to financial or identity theft or prepare them for
a more targeted attack. They also look for ways to install malware that gives them better access to personal data, computer systems or accounts,
themselves. In other cases, social engineers are looking for information that leads to competitive advantage.
Items that scammers find valuable include the following:
- Passwords
- · Account numbers
- Keys
- · Any personal information
- · Access cards and identity badges
- · Phone lists
- · Details of your computer system
- · The name of someone with access privileges
- · Information about servers, networks, non-public URLs, intranet.
How does it work?
Social engineers leverage trust, helpfulness, easily attainable information, knowledge of internal processes, authority that implied or impersonated and
technology to trick you. Often, they will use several small attacks to reach their final goal, bits of information pulled together into a convincing story.
Social engineering is all about taking advantage of others to gather information and infiltrate an organization.
- Information Gathering: A variety of techniques can be used by an aggressor to gather information about the targets. Once gathered, this information can then be used to build a relationship with either the target or someone important to the success of the attack.
- Developing Relationship: An aggressor may freely exploit the willingness of a target to be trusting in order to develop rapport with them. While developing this relationship, the aggressor will position himself into a position of trust which he will then exploit.
- Exploitation: The target may then be manipulated by the ‘trusted’ aggressor to reveal information (e.g. passwords) or perform an action (e.g. creating an account or reversing telephone charges) that would not normally occur. This action could be the end of the attack or the beginning of the next stage.
- Execution: Once the target has completed the task requested by the aggressor, the cycle is complete.
Types of Social Engineering
• Pretexting: Pretexting is when a person uses false or fictitious methods to retrieve a victim’s personal information such as full name,
address, birthdates and social security number. The most common forms of this type of identity theft are over the phone.
Example:
In 2006, HP's chairwoman and some of the members of the board of directors used Pretexting against the board of directors, employees, and journalists to
find the source of the board leaks to the public media. The team of the leak investigation hired a third party firm to obtain the phone records of
suspicious individuals under false pretense without their consents; an action that caused the HP's chairwoman and several directors to lose their jobs.
• Dumpster Diving: Dumpster diving is a technique used to retrieve information that could be used to carry out an attack on a computer
network. Dumpster diving isn't limited to searching through the trash for obvious treasures like access codes or passwords written down on sticky notes.
Seemingly innocent information like a phone list, calendar, or organizational chart can be used to assist an attacker using social engineering techniques
to gain access to the network.
Example:
Workers become complacent and do not think about what they are throwing away. Receipts with signatures, copies of invoices, order forms, and other items
are swept into the trash as workers hurry out of the office on a Friday night or just before a holiday. Another rarely thought of items is anything placed
underneath signatures. When consumers sign receipts there is often a note pad or a desktop calendar that is thrown out at the end of the month. With a
person’s address, phone number, account number, and their signature, the theft is mostly completed. Most homes are easy targets as well. Many people get
pre-approved credit cards and these simple get thrown away and can be used, along with other information, to open fraudulent accounts.
• Phishing: Phishing is a type of Internet fraud that seeks to acquire a user’s credentials by deception. It includes theft of passwords,
credit card numbers, bank account details and other confidential information.
Example:
• Spear Phishing: If traditional phishing is the act of casting a wide net in hopes of catching something, spear phishing is the act of
carefully targeting a specific individual or organization and tailoring the attack to them personally.
Example:
IVR or phone phishing:
IVR or phone phishing also known as "vishing"; this technique uses an Interactive Voice Response (IVR) system to recreate a legit sounding copy of a bank
or other institution's IVR system. The victim is prompted to call in to the "bank" via a phone number provided in order to "verify" information.
Example:
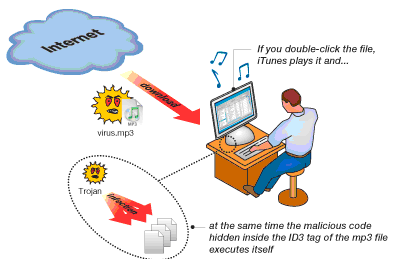
• Trojan horse: A Trojan horse is a malicious application that is designed to enable hackers to remotely access the target computer
system. Trojans may arrive via unwanted downloads on compromised websites or install via online games or other internet-driven applications.
Example:
- Shoulder Surfing: Shoulder surfing refers to using direct observation techniques, such as looking over someone's shoulder, to get information. Shoulder surfing is particularly effective in crowded places because it's relatively easy to observe someone as they:
· fill out a form
· enter their PIN at an automated teller machine or a point of sale terminal
· use a calling card at a public pay phone
· Enter passwords at a cybercafé, public and university libraries, or airport kiosks.
Example:
An example of shoulder surfing is when renting a public locker, some people may choose a four digit PIN code which is the same as that for their credit or
bank access card. A thief who obtains the locker code by shoulder surfing could then access the locker and take and use the credit or bank access card
until the card account is blocked. Avoid using banking codes for other items like lockers, combination locks, etc.
· Diversion Theft: This is when a social engineer convinces a courier or transport company that they're actually you. They then arrange for the parcel to
be arranged to another location nearby. Usually the courier is met at the side of the road by a smiling social engineer who takes the parcel and pretends
to walk towards a house or apartment.
• Forensic analysis: Forensic Analysis is the use of controlled and documented analytical and investigative techniques to identify,
collect, examine, and preserve digital information.
Example:
Obtaining old computer equipment such as hard-drives, memory sticks, DVD/CDs, floppy disks and attempting to extract information that might be of use about
an individual/organization.
• Tailgating: Tailgating involves getting into a physical facility by coercing or fooling staff there, or just walking
in.
Example:
Joe, who has forgotten his passkey into the building, shadows Barb as she ‘keys in’, and slips in after her. Often Barb does not know Joe, or even notice
that Joe has tailgated after her. And more often than not, even if Barb has noticed, she will not turn around and stop Joe from tailgating. She would not
feel comfortable doing that, as it might create a scene in front of others. If Joe is an intruder, he has achieved the first step in his plan - he has
gained physical access into the premises.
- Baiting: Baiting is typically done by leaving a malware infected cd, usb-key in company building, some place that would make it seem as though the item has been dropped by accident. This item might even be labeled with some kind of interesting title so as to encourage the finder to use it on his/her computer to satisfy the curiosity, only to have malware infecting the computer and give the attacker access to sensitive information and/or the company’s internal network.
- Quid pro quo: An attacker offers his victim a gift in exchange for some action or piece of information. The attacker often does not even need to make a deal. By simply providing assistance in some way, an attacker can endear themselves to their victim, making further interrogation a simple matter.
• Reverse Social Engineering: Reverse social engineering is a method where an attacker can get their victims to call them back pertaining
to something an attacker may have previously. Since a victim is calling the attacker, the victim is already at the attacker’s mercy, and it is almost
impossible for the victim to tell that they are being attacked if they have already legitimately made the call back to the attacker.
Example:
The attacker may cause a network failure, show up as a technical support expert just at the right moment, and then help the network operator through the
problem. The operator would think of the attacker as someone of high authority that she could trust and would willingly ask or answer detailed questions
that include confidential information or a way to access it.
• Fake Pop-up: The attacker’s rogue program generates a pop up window, saying that the application connectivity was dropped due to network
problems, and now the user needs to reenter his id and password to continue with his session. The unsuspecting user promptly does as requested, because he
wishes to continue working, and forgets about it.
Ways to prevent Social Engineering
· Management buy-in: Budget for training. HR involved.
· Security policy: A sound security policy will ensure a clear direction on what is expected of staff within an organization.
· Physical security: The use of access badges indicating an individual’s status.
· Education/Awareness: A good training and awareness program focusing on the type of behavior required. This program might even provide users with a
checklist on how to recognize a possible ‘Social Engineering’ attack.
- Good security architecture: No rogue devices.
· Limit data leakage: For example, websites, public databases, Internet registries, and other publicly accessible data sources should only list generic
information, instead of employee names.
· Incident response strategy:. For example, if a user receives a request, he should verify its authenticity before acting on the instructions he has
received.
· Security culture: The creation of a security culture should be considered a long-term investment, which requires a constant effort to maintain and grow.
Conclusion:
Social Engineering is the way an intruder can get access to your information resources without having to be a technical, network or security expert. The
attacker can use many tactics to either fool the victim into providing the information he needs to gain entry, or obtain the information without the
victim’s knowledge.
Social Engineering can be a threat to the security of any organization. It is important to understand the significance of this threat and the ways in which
it can be manifested. Only then can appropriate counter-measures be employed and maintained in order to protect an organization on an ongoing basis.






%2Bdork%2Blist%2Binfosec%2Baffairs.png)
No comments:
Post a Comment